Welcome to a new section of our journey. In this part, we are going to discuss about android applications.
3.1.1 Flow of android applications
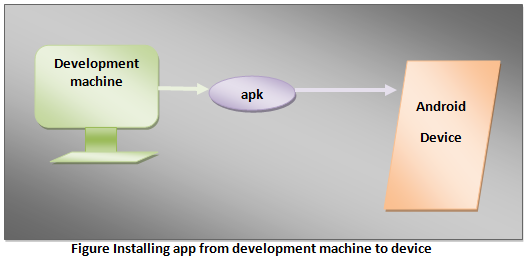
Let us check them out. This flow is starting from our development machine or any app store to the target device. I am breaking them into pieces so that it becomes easy as 1,2,3 for you to grasp the things with minimum struggle. Please go through the following points in sequence.
- The Java language is used to write these applications.
- Both data and resource files are compiled to apk i.e., Android Package by the SDK tools.
- This is an archive file with .apk extension.
Archive file is a set of files which are packed together with the metadata. Files are generally archived for portability and storage. Back up and saving space could be other reasons.
Metadata is data about data, i.e., they describe and gives information about other data.
- APK file contains all the contents of android app.
- Devices powered by android operating system uses this apk file to install the app.
- The Linux system is a multi-user system. Each app in android operating system is considered as a different user.
- Each installed app is assigned a Linux user id which is unique in the system. Permissions are set for all files in app. The system grants these permissions with the user’s consent. Specific User ID designated to specific app can access specified files that have specific permissions. Too long, let’s cut it short and make it simple. If ID has got permission to access then only it is allowed to do so. Other user IDs are allowed to access its information by default.
- Each app has its own virtual machine. This creates a clear boundary between different apps. Each app is isolated from adjacent app running on the device. In other words, each app has an isolated environment to execute without disturbing other apps.
- There is a separate Linux process for each app. Process is started by Android when app’s parts are to be deployed. Process is shutdown when it is not required or system is running short of memory.
You might be thinking what is this process? Well, any program in execution is called a process.
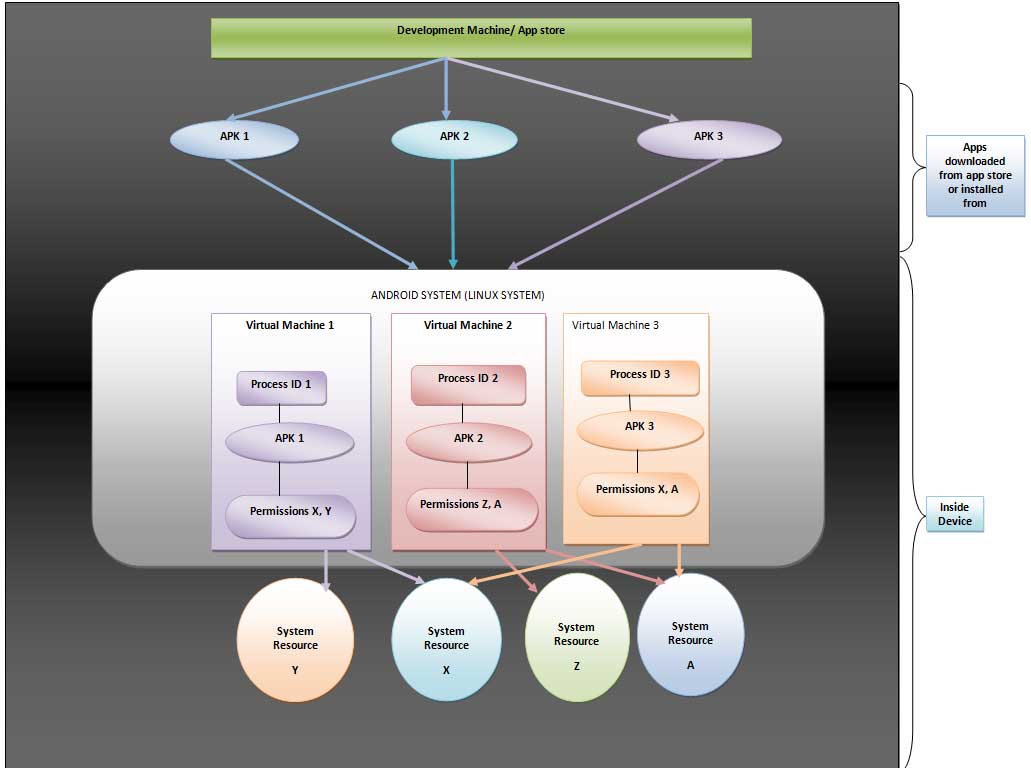
Figure Illustrating principle of least privilege implemented by android
- Principle of least privilege: This principle says that in a particular abstraction layer of a computing environment, the modules like a user or process or program depending upon the subject must be allowed to access only information and resources which are required for fulfillment of its genuine goal. This principle is also called Principle of minimal privilege or principle of least authority in the field of information security.
Android efficiently implements this rule and hence security is incorporated in the system. Each app can access only those resources for which it has permission. It cannot access other parts of the system.
- Sharing: The problem of sharing is taken care of. When two apps need to share their files and resources, they are given same Linux user ID. Not only this, they are signed with the same certificate so that they don’t misuse the permissions. If resources are running short then they can share same VM.
- Other Permissions: Any app can request permission to get access to the system resources like Bluetooth, camera, SD Card, etc. These permissions are requested at the time of installation. For this user is responsible. He/ She decides whether to grant or deny permissions.
3.1.2 Types of Android Applications
User applications generally fall into one of the following categories
- Foreground applications: Games are the best example. In this category applications are useful only when they are in the foreground. They are alive when they are visible, otherwise they are suspended.
- Background applications: These applications don’t have user interaction or they have limited interactivity. Best example is the alarm clock on your device. These are very uncommon apps.
- Intermediate applications: These applications are biased towards one of the above categories of apps. Let me explain this sentence. There are few apps which have limited interactivity and do most of the work in background by remaining hidden. the example is an mp3 music player. Another category will involve lots of user interactions and does some part of computation in the background. Best example is a news app.
- Widgets and Live Wallpaper: Some applications are designed only for the home screen.
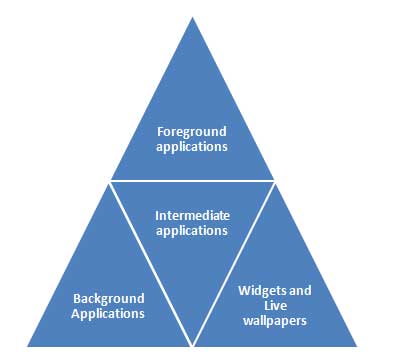
Figure Types of user applications
Now let us move to next sub-section and expand our knowledge.
